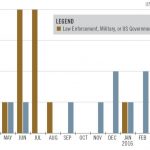
Likely Advanced Persistent Threat (APT) cyber actors have targeted US private sector and government networks since August 2016 with spear phishing campaigns, using newly identified exploits contained within lures related to foreign affairs and the recent US presidential election. The FBI analyzed malicious Microsoft Office documents, a zip archive, a first-stage downloader, a second-stage in-memory-only PNG wrapped malware, and a BAT-initiated PowerShell script associated with the campaigns. This FLASH provides rules and signatures to assist in network defense efforts.