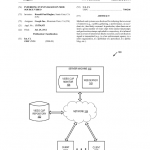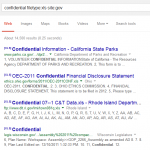
A bulletin issued by the Department of Homeland Security, the FBI and the National Counterterrorism Center earlier this month warns law enforcement and private security personnel that malicious cyber actors can use “advanced search techniques” to discover sensitive information and other vulnerabilities in websites. The bulletin, titled “Malicious Cyber Actors Use Advanced Search Techniques,” describes a set of techniques collectively referred to as “Google dorking” or “Google hacking” that are used to refine search queries to provide more specific results.