Commander’s Handbook for Counter Threat Finance
- 166 pages
- For Official Use Only
- September 13, 2011
This handbook provides an understanding of the processes and procedures being employed by joint force commanders (JFCs) and their staffs to plan, execute, and assess counter threat finance (CTF) activities and integrate them into their joint operation/campaign plans. It provides fundamental principles, techniques, and considerations related to CTF that are being employed in the field and are evolving toward incorporation in joint doctrine.
…
(1) (U//FOUO) Identifying the key personnel associated with the threat financial function. What is their contact information; what are their duties and responsibilities; who do they report to; and what, if any, financial, political, tribal, religious and family ties do they have with the government of the HN and of the countries that surround the HN? What is the relationship between the adversary financial operators and the rest of the adversary organization?
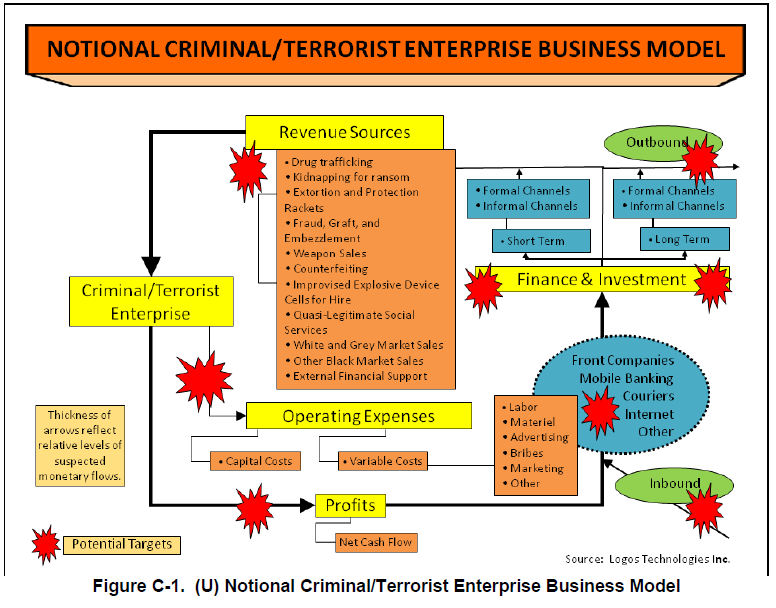
(2) (U//FOUO) Determining how threat financial support networks are organized and controlled and how the money flows through the network from the point of origin to the end user. What are the key nodes in the network? Changes in the distribution of funds through the network can be an indicator of many things to include the establishment of new operational cells, pending adversary offensive operations or a shift in geographic operating areas.
(3) (U//FOUO) Determining which venues the adversary financial operators work from and what areas that they support.
(4) (U//FOUO) Determining the adversary’s cost to operate. What are their fixed and overhead costs? What are their operational costs? What are their special operations costs? Plans and operations drive the requirement to acquire funding. Costs requirements drive fund raising efforts and most funding streams are only capable of producing a certain amount of money. Changes in funding requirements can force the adversary to increase fund raising efforts, which can create undue pressure on the local population and the economy or force the adversary to use new fund raising schemes. Either of these courses of action can expose the adversary financial operators to law enforcement and intelligence collectors.
(5) (U//FOUO) What are their sources of funding (local, area, regional, international, and multinational) and how and when is that money collected?
(6) (U//FOUO) Identifying which financial and natural resources and assets are being exploited by the adversary financial operators (HN, multinational, and US provided).
(7) (U//FOUO) Which funding sources provide the greatest source of revenue to the adversary and what alternatives does the adversary have if that funding source is interdicted?
…