The following manual was publicly posted on the Joint Improvised Explosive Device Defeat Organization’s website.
Joint Publication 3-15.1 Counter-Improvised Explosive Device Operations
- 172 pages
- For Official Use Only
- January 9, 2012
(U) This publication provides joint doctrine for planning and executing counter-improvised explosive device (C-IED) operations. It outlines responsibilities, provides command and control considerations, discusses organizational options, details the C-IED process and attack the network methodology, and introduces models for coordinating with C-IED supporting organizations.
(U) This publication has been prepared under the direction of the Chairman of the Joint Chiefs of Staff. It sets forth joint doctrine to govern the activities and performance of the Armed Forces of the United States in joint operations, and provides the doctrinal basis for the planning and conduct of joint C-IED operations. It provides military guidance for the exercise of authority by combatant commanders and other joint force commanders (JFCs) and prescribes joint doctrine for operations, education, and training. It provides military guidance for use by the Armed Forces in preparing their appropriate plans. It is not the intent of this publication to restrict the authority of the JFC from organizing the force and executing the mission in a manner the JFC deems most appropriate to ensure unity of effort in the accomplishment of the overall objective.
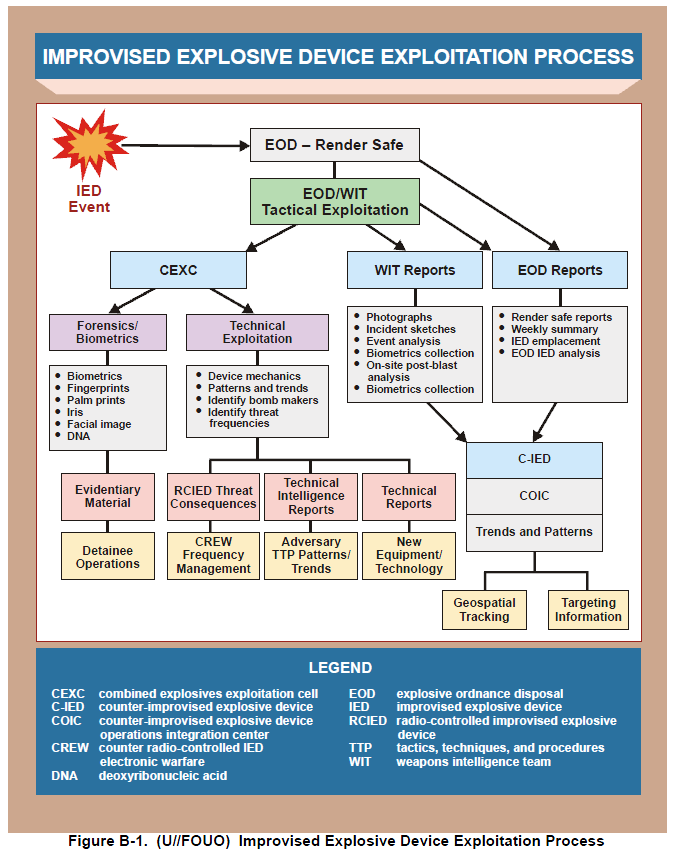
…
3. (U) Attacking the Network—General Considerations
(U) While attacking the adversary’s network is a complex, time-consuming task, raising the adversaries’ cost of IED employment to unacceptable levels can be accomplished through a focused, continuous series of operations designed to disrupt the people, places, processes, and materials that support the IEDs’ design, supply, and employment chain. However, C-IED operations must be accomplished within the context of successfully targeting the broader adversary infrastructure.
a. (FOUO) There is no guaranteed method of defining and codifying targetable activities and major components of an IED network. To avoid detection and attack, adversary networks camouflage and constantly revise, or adapt, their TTP. At the highest echelons, the leadership rarely communicates openly and generally uses trusted aides and couriers to provide broad guidance to subordinates and direct the network. At the lowest echelons, the local cell members are detectable, targetable, and replaceable. Therefore, eliminating individuals only provides temporary and limited solutions to countering IED threats. But as networks function and move resources (information, money, supplies, recruits) from the highest to the lowest echelons, these activities are detectable and targetable. Disrupting the flow of resources is the most reliable way of neutralizing the adversary’s use of IEDs. While ideology may produce recruits, they have to eat, obtain weapons, travel, and build, transport, and emplace bombs. Personnel can be replaced, but
the adversary’s logistical infrastructure and materials often take more time.…