(U//FOUO) TLP: AMBER The Risk: The Multi-State Information Sharing and Analysis Center (MS-ISAC) assesses with high confidence that cyber threat actors routinely target universities, for the purposes of financial gain, notoriety, or entertainment, and often to gain access to personally identifiable information (PII) and/or sensitive research. MS-ISAC believes universities are inherently more vulnerable to cyber targeting than other state, local, tribal, and territorial (SLTT) government entities, due to the non-restrictive research environment with less compartmentalization and less access restriction, which results in more opportunity for infection, and when infection occurs, easier transmission through a network.
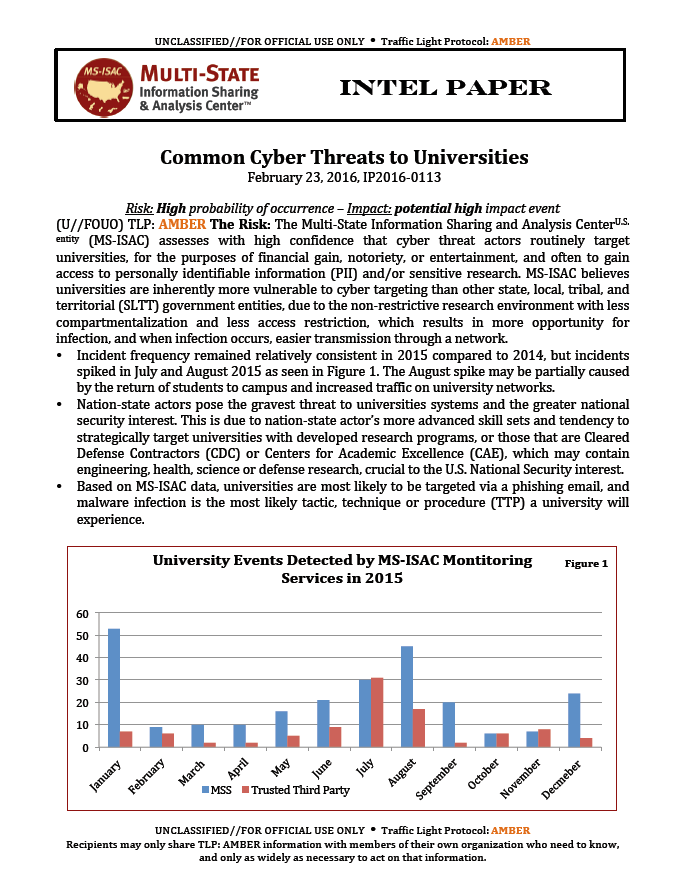
• Incident frequency remained relatively consistent in 2015 compared to 2014, but incidents spiked in July and August 2015 as seen in Figure 1. The August spike may be partially caused by the return of students to campus and increased traffic on university networks.
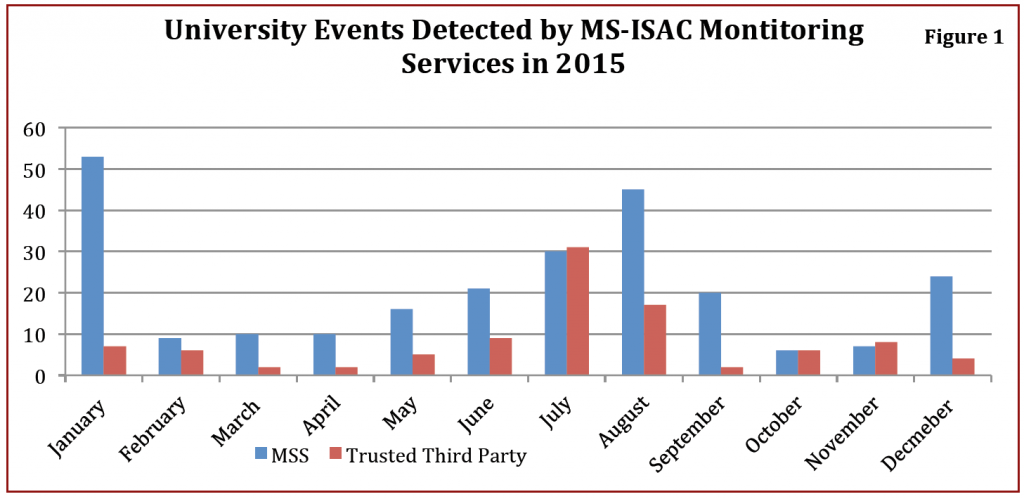
• Nation-‐state actors pose the gravest threat to universities systems and the greater national security interest. This is due to nation-‐state actor’s more advanced skill sets and tendency to strategically target universities with developed research programs, or those that are Cleared Defense Contractors (CDC) or Centers for Academic Excellence (CAE), which may contain engineering, health, science or defense research, crucial to the U.S. National Security interest.
• Based on MS-‐ISAC data, universities are most likely to be targeted via a phishing email, and malware infection is the most likely tactic, technique or procedure (TTP) a university will experience.