The Mad Scientist 2050 Cyber Army project explored the visualization of the Army’s Cyber Force out to 2050 and its ability to address three major objectives of the Army’s Cyberspace Strategy for Unified Land Operations 2025:
What does the cyber environment look like in 2040-2050 (how will cyber influence the environment and the population? What will connecting look like / what will they connect to? What are the drivers influencing this or not)?
How do we build an Army Cyber Force that can dominate the cyber domain in the context of the multi-domain battle concept to gain a position of relative advantage?
How can we build shared goals and expectations as well as develop an understanding of roles and responsibilities in order to build and maintain partnerships with U.S., and international academia, industry, defense departments/ministries and other agencies to enhance cyberspace operations? What new ideas should we be considering?
Co-sponsored by the TRADOC G-2 and the Army Cyber Institute at the United States Military Academy, the 2050 Cyber Army project leveraged submitted papers, an on-line technology survey, and a 13-14 September Mad Scientist Conference that generated the insights synthesized in this report.
Cyber Challenges
As the newest warfighting domain and the first declared domain to be totally man-made, cyberspace poses multiple domain dilemmas for those who would characterize its role in military operations. The cyber domain poses unique physics of time and space, altering our normal perceptions of distance, proximity, and sovereignty while shifting significant portions of the command decision process towards human-machine solution approaches.
Planning predicaments range from the quandary of cyberspace visualization to having to treat cyber “terrain” metaphorically, accounting for the fact that only 4% (the Surface Web) is readily accessible. Intelligence activity is too often forensic and “post-factual” vice “pre-factual,” and our approach to cyber planning authorities is highly asymmetric, both between defensive and offensive operations, and with respect to our adversaries.
The ever-accelerating rate of change in the cyber domain makes cyber-casting daunting indeed. The Department of Defense no longer has a dominant technology development role in shaping the architecture of cyber space. In an environment where battle results are indirect and difficult to observe and quantify, predicting cyber outcomes is problematic even in the near term.
The ubiquity and pervasiveness of the cyber domain presents a categorization conundrum wherein the broad relevance of cyber action in the physical, cognitive and moral dimensions of conflict present endless opportunities for categorization confusion.
Collectively, the cyber challenges generate an “alternative domain” experience that alters our normal expectations with respect to every component of the DOTMLPF-P model.
Strategic Context
Our interests in cyberspace are generally congruent to national interests, but with influences (and impacts) that are more global, reflecting the interconnectivity of cyber infrastructure. Paradoxically, our commitment to ready communication and agile data flows simultaneously affords our adversaries opportunity to undermine our interests while advancing their own.
Digitization and cyber technologies are general-purpose technologies that underpin a growing share of economic activity far beyond the information technology sector. The cyber domain and the digital economy at work within that domain will have increasingly strong economic linkages to the foundations of U.S. power. The economic impacts of the cyber domain, moreover, promise to be disruptive to a stable social fabric with a high potential to accelerate growing gaps in income and mobility.
The role of deterrence in the cyber domain is already a pressing strategic consideration. The problems of ambiguity and attribution in that domain are well known, and there are effectively no rules to constrain cyber conflict. The role of deterrence is not yet conclusively demonstrated in the cyber domain, although the U.S. has announced a two-pronged deterrence policy that will pursue both “deterrence by denial” and “deterrence by cost imposition.”
Army approaches to future cyber conflict will have to account for a broad, multi-echeloned array of cyber strategies. Higher level strategies include The White House International Strategy for Cyberspace and the DoD Cyber Strategy; within the Army the strategic context is addressed by the Army Cyberspace Strategy for Unified Land Operations in 2025, and the Army Cyber Center of Excellence Strategy.
To practice effective mission command, sustain its forces, provide critical intelligence, and communicate over the horizon, a nation must – of necessity – be a cyber power. The “barriers to entry” for cyber power status, however, are relatively low. Moreover, cyber power demonstrates a destabilizing capability / vulnerability paradox: the greater the reliance on advanced cyber capabilities, the greater vulnerability to disruption, diversion, and destruction.
DOTMLPF-P Insights
Because cyber theory is relatively immature, cyber doctrine has relatively weak and disputed theoretical underpinnings for categorization, principles, and similar tools of doctrine. Fundamental doctrinal ideas such as “levels of war” and “maneuver” struggle to migrate to the cyber domain; while traditional doctrinal imperatives to generate combined arms synergy and to seize, retain, and exploit the initiative maintain their primacy.
Organization solutions for the 2050 Cyber Army have begun with the stand up of the Cyber Mission Force, but the Army’s future organizational approaches must account for technology trends that are simultaneously both centralizing and decentralizing. Organizational solutions in the cyber domain will include extensive use of interdisciplinary teaming and partnering. A fundamental organizational debate looms as proposals surface for a Cyber Service.
Cyber warriors are “knowledge workers” and as such will need more than “training;” they need a strong education in cyber fundamentals in order to deal with the dynamic complexities of the cyber domain. Cyber training and education will be significantly self-directed, modular, open-loop, and lifelong.
There is general consensus that the most significant dimension of cyber material is the ‘software’ vice the ‘hardware.’ As an increasingly pervasive Internet of Things is enabled by artificial intelligence (AI), we will enter an era of Sentient Tools, the next phase of development for computational systems, smart cities and environments, autonomous systems, and other advanced technologies. Current vulnerabilities allowed by design are correctable, and several disruptive materiel solutions may mitigate some future cyber vulnerabilities.
Future Commanders must be as adept at deploying cyber effects as they are at delivering physical effects. Their leadership and education must address desirable attributes and skills, and be broad enough to enable their ability to conceptualize rapidly and develop creative, feasible solutions to complex challenges.
Competition for talent in the cyber field will be fierce, and promises to upend our most cherished personnel assumptions about recruitment and retention. Motivators extend beyond monetary compensation to include patriotism, an interesting problem space, and the desire to make an impact.
Because of their ubiquitous nature and transformational characteristics, cyber infrastructure facility impacts on the future of conflict will be exponential vice merely additive. The centralization trend of some cyber technologies positions these central facilities as high pay-off targets that may be difficult to repair or replace.
The consequences and visibility of key cyber policy issues like data privacy and security, surveillance, and internet management have grown and are addressed at levels far above the Army; these policies nonetheless directly impact Army preparation for and execution of cyber operations. With most policy and precedents relatively immature, their evolution out to 2050 will be extensive.
Cyber Futures
“Cyber-casting” is problematic, but a series of attributes describe that elusive future:
Ubiquity. Cyber will be “everywhere” and so pervasive that in the future “cyber is no longer cyber.”
Volatility. The pervasiveness and leverage of cyberspace structure will likely have a destabilizing impact on global – and local – stability.
Uncertainty. The explicit mechanism of connectivity and “cause-and-effect” in cyberspace infrastructure will be buried in the sheer mass of users, nodes, connections and data within it.
Complexity. With “cause-and-effect” relationships not readily apparent, the quantity of those relationships will shift a “complicated” system into the “complex” category.
Convergence. As data and digitization continue to move beyond information and technology communication to all aspects of our physical, cognitive and social experiences, a dominant attribute of the cyber future will be convergence.
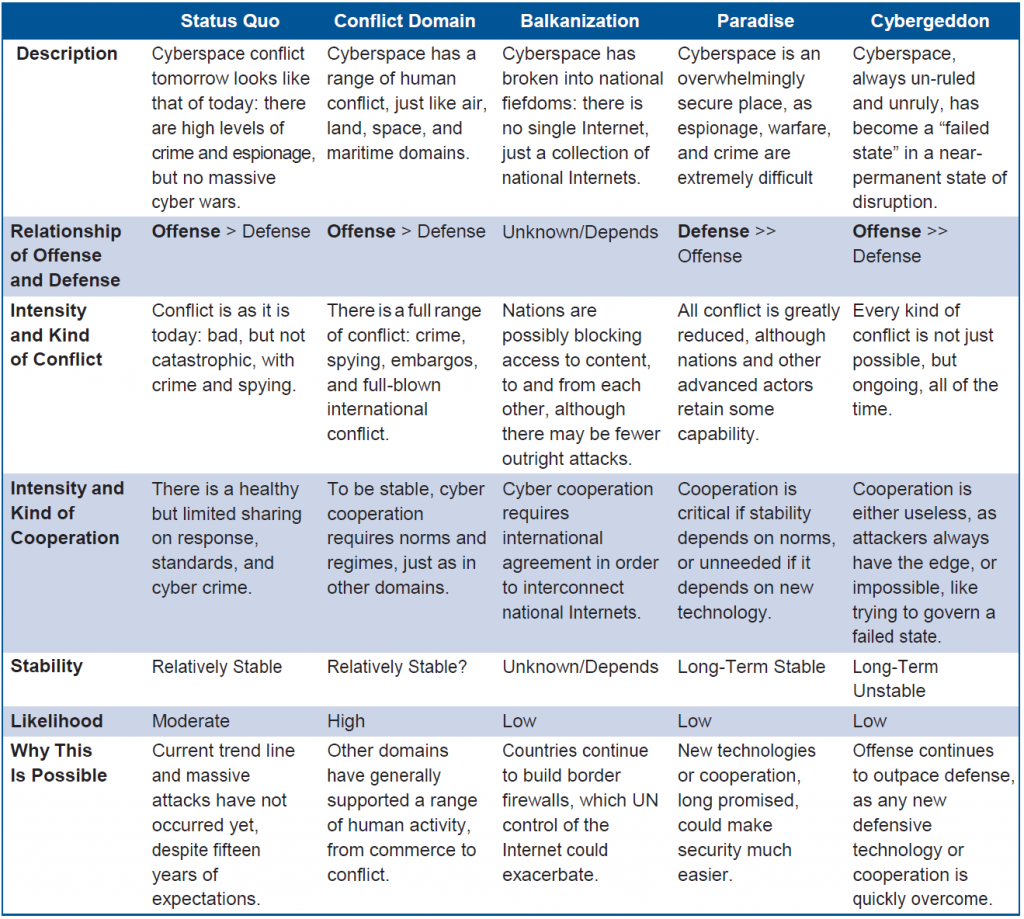
Five potential alternative cyber futures define the range of potential cyber domain environments out to 2050. They include:
“Status Quo.” Cyberspace conflict tomorrow looks like that of today: there are high levels of crime and espionage, but no massive cyber wars.
“Conflict Domain.” Cyberspace has a range of human conflict, just like air, land, space and maritime domains.
“Balkanization.” Cyberspace breaks down into national fiefdoms: there is no single internet, just a collection of national internets.
“Paradise.” Cyberspace is an overwhelmingly secure place, where espionage, warfare, and crime are extremely difficult.
“Cybergeddon.” Cyberspace, always un-ruled and unruly, has become a “failed state” in a near-permanent state of disruption.
…