
A November 2016 slide deck from the Governmental Advisory Committee Public Safety Working Group of ICANN related to initiatives to improve the accuracy of data in the WHOIS system of domain and IP address ownership/registration.

AT&T shall provide certain data and reports to the Government Agency, as specified in section 3.0 Tasks. The data that will be provided to the Government Agency is limited to telecommunications information and records and analysis thereof. In addition to the items provided in section 3.0 Tasks, AT&T shall provide expedited processing of information requested by compulsory legal requests (collectively referred to as Legal Process) regarding telecommunications information and records under the AT&T’s ownership or control.

The purpose of this white paper is to provide an in-depth examination of ABI-like analytic techniques that were developed, refined and employed to successfully support multiple, high-level, but dissimilar interagency law enforcement investigations over an extended period of time. The premise of this paper is that, as the Intelligence Community developes a strategy, framework and roadmap for enterprise-wide adoption of ABI, lessons learned from the law enforcement community are worthy of examination and possible incorporation into the IC strategy for ABI.

These Guidelines are provided for use by law enforcement or other government entities in the U.S. when seeking information from Apple Inc. (“Apple”) about users of Apple’s products and services, or from Apple devices. Apple will update these Guidelines as necessary. This version was released on September 29, 2015.

Online radicalization to violence is the process by which an individual is introduced to an ideological message and belief system that encourages movement from mainstream beliefs toward extreme views, primarily through the use of online media, including social networks such as Facebook, Twitter, and YouTube. A result of radical interpretations of mainstream religious or political doctrines, these extreme views tend to justify, promote, incite, or support violence to achieve any number of social, religious, or political changes.

One fact should not be lost in this discussion. As has always been the case, new methods of authenticating identity, like biometric identification, are necessary to augment existing conventions and meet current needs. Biometric technologies do this and, as a major privacy‐enhancing technology, preserve privacy at the same time. The facial template itself, like other biometric templates, provides no personal information. Indeed, protecting the non‐biometric personal information is enhanced through the use of biometric verification of identity to limit data access to only authorized persons. Biometrics can provide a unique tool to protect and enhance both identity security and privacy and to protect against fraud and identity theft, especially as a factor in identity verification. When your personal data are protected by access mechanisms that include one or more biometric factors, it becomes much more difficult for someone else to gain access to your personal data and applications because no one else has your unique biometric attributes. This enables legitimate access and reduces the risk that a person can steal your identity and, posing as you, collect benefits; board an airplane; get a job; gain access to your personal data, etc.
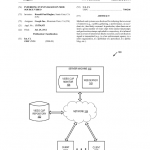
Methods and systems are disclosed for inferring that an event of interest (e.g., a public gathering, a performance, an accident, etc.) has likely occurred. In particular, when there are at least a given number of video clips with similar timestamps and geolocation stamps uploaded to a repository, it is inferred that an event of interest has likely occurred, and a notification signal is transmitted (e.g., to a law enforcement agency, to a news organization, to a publisher of a periodical, to a public blog, etc.).
Tax returns for the CIA’s venture capital firm In-Q-Tel, Inc. spanning from tax year 2000-2011.

Scans of all invoices related to the City of Oakland’s contract with Science Applications International Corporation for the construction of the City/Port of Oakland Joint Domain Awareness Center. The documents were collected in a binder held by the City of Oakland and obtained via a public records request made by members of Occupy Oakland. The invoices are organized by month and range in date from March to July 2013.

Snapchat is a smart phone application accessed through the iPhone AppStore or Google Play. The application provides a new way to share moments with photos and videos. The purpose of this guide is to familiarize law enforcement agencies with the categories of information available from Snapchat and the specific le8al process necessary to obtain that information. Snapchat is committed to assisting law enforcement investigations to the fullest extent allowed by applicable law. In addition to this guide, Snapchat also provides phone and email support to law enforcement agencies for both emergency and non-emergency inquiries. Contact information for law enforcement support is listed on the cover of this guide.

Two presentations from the Gamma Group describe the company’s FinFisher and 3G-GSM tactical interception and target location surveillance products. The presentations were anonymously posted online and are reportedly from 2011 discussions between Gamma and the German State Criminal Police Offices (Landeskriminalamts).
A table describing Research in Motion/Blackberry requirements for disclosure of user data to law enforcement. The chart shows what legal process is required to request user data, the type of data each process can typically obtain and the legal authorities authorizing each form of request.
On May 21, 2013, the Permanent Subcommittee on Investigations (PSI) of the U.S. Senate Homeland Security and Government Affairs Committee will hold a hearing that is a continuation of a series of reviews conducted by the Subcommittee on how individual and corporate taxpayers are shifting billions of dollars offshore to avoid U.S. taxes. The hearing will examine how Apple Inc., a U.S. multinational corporation, has used a variety of offshore structures, arrangements, and transactions to shift billions of dollars in profits away from the United States and into Ireland, where Apple has negotiated a special corporate tax rate of less than two percent. One of Apple’s more unusual tactics has been to establish and direct substantial funds to offshore entities in Ireland, while claiming they are not tax residents of any jurisdiction. For example, Apple Inc. established an offshore subsidiary, Apple Operations International, which from 2009 to 2012 reported net income of $30 billion, but declined to declare any tax residence, filed no corporate income tax return, and paid no corporate income taxes to any national government for five years. A second Irish affiliate, Apple Sales International, received $74 billion in sales income over four years, but due in part to its alleged status as a non-tax resident, paid taxes on only a tiny fraction of that income.
There is provided a device and system for restraining detainees through devices attached to the detainees and configured to administer electrical shocks when certain predetermined conditions occur. Restraining devices may be activated by internal control systems or by external controllers that transmit activation signals to the restraining device. External controllers may be actuated by an external controlling entity such as a detention guard or other person or system, or may be controlled by an enabling signal sent by wired or wireless connections to the controller. There is also provided a system for detainee restraint where multiple detainees may be restrained collectively or individually in a controlled environment such as a detention facility, a jail, or a detainee transport vehicle.
The advent of set-top box devices and other media content access devices (“access devices”) has provided users with access to a large number and variety of media content choices. For example, a user may choose to experience a variety of broadcast television programs, pay-per-view services, video-on-demand programming, Internet services, and audio programming via a set-top box device. Such access devices have also provided service providers (e.g., television service providers) with an ability to present advertising to users. For example, designated advertisement channels may be used to deliver various advertisements to an access device for presentation to one or more users. In some examples, advertising may be targeted to a specific user or group of users of an access device.
Harris Corporation’s standard terms and conditions for the sale of their wireless surveillance products including the AmberJack, StingRay, StingRay II, Harpoon and KingFish products. The terms and conditions document was included in a contract signed with Tempe, Arizona on October 8, 2012 for $60,321.15 worth of surveillance software, equipment and training.
With internet traffic growing exponentially, attacks on government and commercial computers by cyber terrorists and rogue states have escalated. Those wishing harm have espionage programs targeting the data systems used by the United States and allies. Drug traffickers and weapons dealers use the internet with encrypted communications. To counter these activities, the National Security Agency, an agency of the U.S. government, is building a fortified data center deep inside a mountain in Utah. This complex will house the world’s most sophisticated supercomputers dedicated to code breaking and data traffic analysis. Another site will eventually take delivery of the latest Cray supercomputer called Cascade to support the NSA’s need to crack codes faster to protect the nation and its allies.
Trap Wire dramatically increases the ability to detect pre-attack preparations and to take appropriate action to detect, deter and intercept tenorist attacks. A visual monitor of the entire system-a map with dynamic status indicators for each entity connected to the Trap Wire network- facilitates the ability of decisionmakers to absorb vast quantities of information quickly and efficiently. The dynamic status indicators show the threat level at each facility and highlight those that have moved to a higher threat level over the preceding 24 hours. Security officials can thus focus on the highest priorities first, taking a proactive and collaborative approach to defense against attacks. The information collected by Trap Wire can also be shared with law enforcement agencies to assist in their counterterrorism efforts.
A presentation from Victoria Sheckler, Deputy General Counsel of the Recording Industry Association of America, was presented at an International Federation of the Phonographic Industry meeting in Panama in April 2012. It contains information on an upcoming effort by internet service providers to police their users’ sharing of copyrighted material called the Copyright Alert System. The presentation also discusses other voluntary measures such as agreements by payment processors to stop doing business with sites that are “repeat offenders” and efforts to encourage domain name registrars to enforce stricter “whois” policies.
On May 20-21, 2012, Chicago will host the 25th North Atlantic Treaty Organization (NATO) Summit – the first NATO Summit in the U.S. held outside of Washington, DC. Delegations from 28 NATO Member Countries, 24 International Security Assistance Force (ISAF) Partner Countries, and six other nations and international organizations will participate in the Summit. The Summit will bring economic benefits in the form of spending, tax revenues, employment, hotel guests, tourism, and broader global attention. Over 7,500 delegates and 7,300 staff, press, and other dignitaries are expected to attend the Summit. In addition, planning for the Summit prompted visits and spending by delegations during advance trips to Chicago. Building on the momentum of the Summit, many Chicago organizations have planned events that will generate additional economic impacts for the City. These ancillary events are expected to draw thousands of additional speakers, staff, attendees, and members of the media.
Between May 2007 and May 2010, as part of its Street View project, Google Inc. (Google or Company) collected data from Wi-Fi networks throughout the United States and around the world. The purpose of Google’s Wi-Fi data collection initiative was to capture information about Wi-Fi networks that the Company could use to help establish users’ locations and provide location-based services. But Google also collected “payload” data–the content of Internet communications–that was not needed for its location database project. This payload data included e-mail and text messages, passwords, Internet usage history, and other highly sensitive personal information.
A 2010 price list for Harris Corporation wireless surveillance products was included in contract documentation for the purchase of multiple KingFish Dual Mode wireless measurement systems that went to Maricopa County, Arizona.