
A document published on the website of the Mexican Instituto Nacional de Migración (National Institute of Migration) in July 2013 detailing Latino gang tattoos.

Terrorists may engage in sabotage, tampering, or vandalism as part of an attack or to gain access to restricted areas, steal materials, or provoke and observe security responses. For example, the 1Oth edition of al-Qa’ida in the Arabian Peninsula’s Inspire magazine suggests torching parked vehicles and causing automobile accidents by using lubricating oil or nails driven through wooden boards as simple tactics to cause both casualties and economic damage.

To reduce deficiencies in security, DoD Directive 5200.43 established the Defense Security Enterprise (DSE) Executive Committee (ExCom). The ExCom is the senior-level governance body for the strategic administration and policy coordination of the DSE. The ExCom created and tasked the DSE Advisory Group (DSEAG) to plan, coordinate, and prioritize decisions for the ExCom and establish, oversee, and launch project teams. These project teams receive tasks from the DSEAG, research an issue, and recommend a plan of action.

Impersonation by assuming the identity, behavior, or appearance of first responders can allow terrorists access to restricted or secure locations, including the scene of emergencies when unchallenged. This access can allow terrorists the ability to conduct pre-operational surveillance or carry out a primary attack or a secondary attack against first responders. The method of impersonation may not be limited to the use of uniforms, clothing, badges and identification; civilian vehicles may be accessorized to appear as legitimate emergency vehicles.

On the basis of the evidence obtained during our investigation of the Ghouta incident, the conclusion is that, on 21 August 2013, chemical weapons have been used in the ongoing conflict between the parties in the Syrian Arab Republic, also against civilians, including children, on a relatively large scale.

DHS and its operational components have recognized the value of using social media to gain situational awareness and support mission operations, including law enforcement and intelligence-gathering efforts. However, additional oversight and guidance are needed to ensure that employees use technologies appropriately. In addition, improvements are needed for centralized oversight to ensure that leadership is aware of how social media are being used and for better coordination to share best practices. Until improvements are made, the Department is hindered in its ability to assess all the benefits and risks of using social media to support mission operations.

Reducing corruption and increasing accountability are important components of the U.S. reconstruction strategy in Afghanistan. Since 2002, the United States has appropriated over $96 billion for reconstruction assistance in Afghanistan and, as part of that assistance, has designated numerous programs or activities to directly or indirectly help strengthen the ability of Afghan government institutions to combat corruption. In 2010, in line with a commitment to provide more assistance directly to the Afghan government, the United States and other donors committed, in part, to providing technical assistance to develop the Afghan government’s capacity to reduce corruption. The ability of the Afghan government to deliver services to its citizens without the illicit diversion of resources is crucial to the country’s development and the government’s standing as a legitimate, sovereign authority. Further, as Afghanistan subsequently enters a transformation phase during which it will need to rely on progressively smaller amounts of funding from international donors, it must work to ensure that the revenue it generates is not susceptible to graft and corruption.

The reference provides warning and other appropriate measures to guard against the outbreak of nuclear war, either as a result of planned intercontinental ballistic missile (ICBM) or submarine-launched ballistic missile (SLBM) launches, or unauthorized or unexplained accidents or incidents involving a US space launch or event or implying a possible threat of a nuclear attack. Because the highest national importance is attached to agreements with the Russian Federation, the United States intends to prevent any event that would violate the agreements and implement actions minimizing the effect of any incident that might occur.

An updated policy manual for the FBI National Data Exchange (N-DEx) released August 28, 2013. The manual was updated to include substantial additions to the regulations governing use of information within the system and the maintenance of records for later auditing of law enforcement agencies’ access to the system.

Trends in the operational environment continue to indicate that cyberspace and the electromagnetic spectrum (EMS) will remain important entities within the operational environment for the foreseeable future. The Army understands the importance of cyberspace and the electromagnetic spectrum to human societies in general, and to military operations specifically. Army leaders and Soldiers must possess an in-depth understanding of this contest, and how to gain, maintain, and leverage advantages in this contest. To this end, the Army Concept Framework recognizes an increasingly important aspect to military operations: the cyber/electromagnetic contest (C/EM contest).

This publication of Treasury’s Office of Foreign Assets Control (“OFAC”) is designed as a reference tool providing actual notice of actions by OFAC with respect to Specially Designated Nationals and other persons (which term includes both individuals and entities) whose property is blocked, to assist the public in complying with the various sanctions programs administered by OFAC. The latest changes to the SDN List may appear here prior to their publication in the Federal Register, and it is intended that users rely on changes indicated in this document.

An August 2013 presentation from the Texas Department of Public Safety Intelligence & Counterterrorism Division focusing on suspicious activity reporting in relation to critical infrastructure, particularly dams. The presentation is noteworthy for its reference to the use of TrapWire, a private surveillance product designed to correlate suspicious activity across a variety of domains to detect per-operational indicators of terrorist activity.

The Syrian Electronic Army (SEA), a pro-regime hacker group that emerged during Syrian anti-government protests in 2011, has been compromising high-profile media outlets in an effort to spread pro-regime propaganda. The SEA’s primary capabilities include spearphishing, Web defacements, and hijacking social media accounts to spread propaganda. Over the past several months, the SEA has been highly effective in compromising multiple high-profile media outlets.

The United States Government assesses with high confidence that the Syrian government carried out a chemical weapons attack in the Damascus suburbs on August 21, 2013, resulting in a large number of casualties, including the deaths of 1,429 people, among them 426 children. We further assess that the regime used a nerve agent in the attack.

Two presentations from the Gamma Group describe the company’s FinFisher and 3G-GSM tactical interception and target location surveillance products. The presentations were anonymously posted online and are reportedly from 2011 discussions between Gamma and the German State Criminal Police Offices (Landeskriminalamts).

The Hemisphere Project is coordinated from the Los Angeles Clearinghouse and is funded by ONDCP and DEA. Hemisphere provides electronic call detail records (CDRs) in response to federal, state, and local administrative/grand jury subpoenas. The Hemisphere database contains CDRs for any telephone carrier that uses an AT&T switch to process a telephone call. Hemisphere is an unclassified program. Hemisphere provides de-confliction within the Hemisphere database. 4 billion CDRs populate the Hemisphere database on a daily basis.

The following definitions align key cyberspace operations (CO) concepts with doctrinally accepted terms and definitions used in the other joint operational domains. For explanatory purposes, in each case, the current Information Operations (IO) doctrinal definition for some aspect of CO is presented, followed by its conventional analogue, if any, and the current terminology it would replace.

This functional concept details capabilities and effects necessary to perform operational cyberspace functions desired by the warfighter, from the present through 2030. This concept broadly describes how AFSPC intends to conduct cyberspace operations in support of both joint and AF operations of all types, and provides a foundation for developing more detailed concept documents. Moreover, AFSPC will use this concept, along with emerging joint guidance, to organize, train, and equip forces to conduct cyberspace operations. Finally, this concept provides the operational perspective to underpin the many activities necessary to realize the AF institutional vision for a mature set of cyberspace capabilities.

The United States Air Force (USAF) Blueprint for Cyberspace provides commander’s guidance and intent, identifies opportunities and delineates objectives and strategies that will shape USAF actions over the next five years. This document describes the first phase of a two-phase approach. It defines specific actions to align cyber activities and functions, to evolve and integrate the unique capabilities the USAF brings to the joint fight, and to build cyberspace operational capacity.
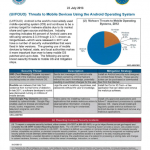
Android is the world’s most widely used mobile operating system (OS) and continues to be a primary target for malware attacks due to its market share and open source architecture. Industry reporting indicates 44 percent of Android users are still using versions 2.3.3 through 2.3.7-known as Gingerbread-which were released in 2011 and have a number of security vulnerabilities that were fixed in later versions. The growing use of mobile devices by federal, state, and local authorities makes it more important than ever to keep mobile OS patched and up-to-date.