
A January 2016 presentation from the U.S. Computer Emergency Readiness Team Cyber Threat Information Sharing Branch regarding their operations investigating and countering botnets.

Cyber targeting of the ESS will likely increase as ESS systems and networks become more interconnected and the ESS becomes more dependent on information technology for the conduct of daily operations—creating a wider array of attack vectors for cyber targeting. Independent researchers have already reported on the widespread availability of vulnerabilities and attack vectors for critical hardware and software that is used in this sector extensively. Such vulnerable systems include call-center communications-management software, closed-circuit TV camera systems, interactive voice response systems, and emergency alert systems—particularly wireless emergency alert systems.

Despite efforts to counter violent extremism, the threat continues to evolve within our borders. Extremism and acts of targeted violence continue to impact our local communities and online violent propaganda has permeated social media. Countering these prevailing dynamics requires a fresh approach that focuses on education and enhancing public safety—protecting our citizens from becoming radicalized by identifying the catalysts driving extremism.
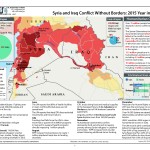
Over 15 million people have been displaced due to conflict in Syria and Iraq. The Syrian Observatory for Human Rights documented at least 260,000 Syrians killed in the conflict since it began in 2011. The UN reported at least 26,600 Iraqis killed from 2014-2015 due to acts of terrorism and violence.

This Joint Intelligence Bulletin (JIB) is intended to provide information on the recent arrest of 11 domestic extremists for conspiracy to impede officers of the United States from discharging their official duties through force, intimidation, or threats, in violation of 18 USC §372. This JIB is provided by the FBI and DHS to support their respective activities and to assist federal, state, local, tribal, and territorial government counterterrorism and law enforcement officials in deterring, preventing, or disrupting terrorist attacks against the United States. As in any criminal case, defendants are presumed innocent until proven guilty in a court of law.

Shabaab al-Mujahideen (aka al-Shabaab, aka Mujahideen Youth Movement) is the Salafist-Jihadist off-shoot of the Mogadishu-based Islamic Courts Union (ICU). Al-Shabaab’s leaders maintain connections with al-Qaeda, and receives financial, logistical, and rhetorical support. The group is fighting the internationally recognized TFG for control of Somalia’s southern cities, and ultimately seeks to control the entire Horn of Africa. Al-Shabaab employs IEDs in support of its broader strategy of ousting the TFG and the contingent of African Union peacekeepers (mostly from Uganda and Burundi) protecting the TFG, called the African Mission in Somalia (AMISOM). As a result, their IEDs target TFG and AMISOM personnel and operations. Al-Shabaab will continue to focus its IED efforts against TFG and AMISOM operations, primarily in Mogadishu, as part of an al-Qaeda-inspired strategy of attrition and exhaustion.

Despite official statistics showing a decrease in the number of arrests related to Salafist-jihadist activity, EU-based security services have thwarted numerous IED-centered plots since 2003. Many of the EU plots involve al Qaeda-networked terrorists in Afghanistan and Pakistan, and included plots in Spain, Germany, Italy, Belgium, and the United Kingdom (UK). Two recent plots are representative of the current IED threat in the EU: the Sauerland plot in Germany (2007) and the Barcelona plot in Spain (2008).

Recent events surrounding the occupation of the Malheur Wildlife Refuge in Harney County Oregon, have culminated in the fatal confrontation of Northern Arizona rancher, LaVoy Finicum. His funeral services will be held on 05 FEB 2016, in Kanab, UT. Finicum will be buried on 06 FEB 2016, close to his Arizona ranch in Cane Beds, AZ. While no credible threats to law enforcement are present at this time, armed extremists are expected to travel through UT; some of which may see this event as a tipping point, and potentially shift toward more violent action. A number of individuals, several of whom were present at the Burns, OR occupation, are planning caravans from UT and NV to travel to the funeral in show of support.

In September 2014, The Islamic State of Iraq and Syria (ISIS) released a propaganda video encouraging its followers to murder “intelligence officers, police officers, soldiers and civilians.” The video was re-released in January 2015 and specifically named the United States, France, Australia and Canada as targets. Now, first responders have an additional threat: Impersonation and misrepresentation by terrorists as first responders. The impersonators main goals are to further their attack plan and do harm to unsuspecting citizens as well as members of the emergency services community.

It has now been five years since the events of the “Arab Spring,” and initial optimism about lasting democratic reforms and an era of lessened tensions has been replaced by fear and skepticism. Many countries are now experiencing greater instability and violence than before. The vestiges of Al Qaeda in Iraq have morphed into the Islamic State of Iraq and al-Sham (or the Levant)—ISIS or ISIL, sweeping through Iraq and Syria and leaving behind much death and destruction. The growth of violent extremism initiated by Al Qaeda and its radical interpretation of the Islamic ideology is continuing. ISIL’s deft manipulation of social media to compel and mobilize individuals to act out violently is both remarkable and frightening.

This White Paper makes a significant contribution to the study of terrorist behavior in general and ISIL behavior in particular. Unique in this work is the melding of neuroscientific considerations about the basic structures and functions of the brain with social and cultural influences in order to provide a holistic insight into the motivations for terrorist behaviors. Importantly, this paper also explores the relationship between the narratives that support terrorist behavior and the neuro-cognitive processes that contribute to those behaviors. That relationship is accurately portrayed as symbiotic in the sense that one can only truly understand seemingly aberrant behavior if one understands the continuous ebb and flow of chemical and cultural influences that are manifested in an individual’s actions.

Dam safety incidents can occur at any point during a dam’s lifetime, but the most common period of dam failure is the first 5 years of operation. The United States Society of Dams conducted a study in 2009 of 1,158 national and international dam failures and safety incidents and found that 31 percent of safety incidents occur during construction or within the first 5 years of operation. The most common causes of failure are overtopping, piping, and foundation defects. Overtopping caused by flooding and high-water events accounts for 34 percent of dam failures in the United States. Erosion caused by overtopping can compromise embankments and lead to failure. The risk of overtopping increases if the spillway design is inadequate, debris causes spillway blockage, or the dam crest settles.

Most locks are designed to last for 50 years, but 54 percent of IMTS locks are more than 50 years old, and 36 percent are more than 70 years old. Many of these locks are in need of repair and replacement, and some lack basic maintenance. Concrete is crumbling at some locks, and some have not been painted in 25–30 years, increasing the risk of corrosion. Locks lacking maintenance or in need of repair and replacement are more likely to have unscheduled closures. Unscheduled closures are more costly than scheduled closures, because vessel operators and companies are unable to plan to offset the delays from these incidents. The annual number of unscheduled lock closures has steadily increased since 1992. Fewer than 7,000 unscheduled closures occurred every year before 2000, and more than 7,000 occurred every year after 2000, peaking in 2008 with 13,250.

This document presents an overview of terrorism threats and terrorist methodologies to assist OPSEC managers in evaluating the threat and managing terrorist risks to organizations and personnel. As in other areas of security and intelligence concern, proper application of the OPSEC process in evaluating threat and risk1 helps an organization to make informed decisions on conducting its mission-critical activities without becoming unduly vulnerable.

Social engineering, an age old threat, continues to play a significant role in successful attacks against people, enterprises, and agencies. The advent of the Internet, its diverse and increased use, and the reliance on it by almost every element of society, amplifies social engineering opportunities. Cybercriminals enjoy an expansive attack surface, novel attack vectors, and an increasing number of vulnerable points of entry. Threat actors, both cyber and physical, continue to leverage social engineering due in part to its high rate of success. Security experts believe complex social engineering threats will continue across all vectors and attack levels will continue to intensify.

The Department of Homeland Security Office of Cyber and Infrastructure Analysis (DHS/OCIA) produces Critical Infrastructure Security and Resilience Notes in response to changes in the infrastructure community’s risk environment from terrorist activities, natural hazards, and other events. This product summarizes the findings related to highway bridges that were identified in the National Risk Estimate on Aging and Failing Critical Infrastructure Systems released by DHS/OCIA in December 2014.

The violent militia extremist movement in the United States is comprised of a collection of distinct, but organized, paramilitary groups that have engaged in violent criminal activities and terrorism-related plots to advance their anti-government beliefs. Individual violent militia extremists have been convicted of a range of firearms and explosives violations and criminal conspiracy charges. The violent militia extremist movement is a subset of the larger militia movement; many groups and individuals involved in the overall militia movement do not commit criminal or violent acts.

The abuse of illicit drugs, specifically heroin and cocaine, as well as the opioids fentanyl and oxycodone, has contributed to an increase in drug-related deaths in Philadelphia over the last decade. Specifically, drug-related overdose deaths in Philadelphia have risen 43 percent since 2009, with a corresponding 45 percent increase in heroin-positive toxicology test results.