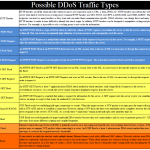
A January 2014 bulletin from the Department of Homeland Security National Cybersecurity and Communications Integration Center on distributed denial-of-service attacks and mitigation methods.

Law enforcement continues to see reporting of malicious cyber actors using fake help desk scams, also known as technical support scams. These scams, if successful, seek to compromise and take control of computer systems. Malicious cyber actors send users an e-mail or they make cold calls, purportedly representing a help desk from a legitimate software or hardware vendor. The malicious cyber actors try to trick users into believing that their computer is malfunctioning—often by having them look at a system log that typically shows scores of harmless or low-level errors—then convincing them to download software or let the “technician” remotely access the personal computer to “repair” it.

Since at least January 2012, criminals are using telephony-based denial-of-service (TDoS) combined with extortion scams to phone an employee’s office and demand the employee repay an alleged loan. If the victim does not comply, the criminals initiate TDoS attacks against the employer’s phone numbers. TDoS uses automated calling programs—similar to those used by telemarketers—to prevent victims from making or receiving calls.

Threats to Federal information systems are rising as demands for sharing of information and intelligence between Federal Departments and Agencies increase. It is essential that the Federal Government devise an approach that addresses both challenges without compromising the ability to achieve either objective. Developing a common governance framework and set of Identity, Credential, and Access Management (ICAM) capabilities that enhance the security of our systems by ensuring that only authorized persons and systems from different Federal components have access to necessary information is a high priority. The Federal Identity, Credential and Access Management (FICAM) Roadmap and Implementation Guidance was developed to address the need for secure information sharing capabilities across the breadth of the Federal Government.

Over the past ten years, the Federal Government has made concerted advances in the development and implementation of Identity, Credential, and Access Management (ICAM). This progress includes capabilities designed to promote interoperability, assured information sharing, and efficiencies of scale across all agencies within the Federal Government. Recently, several high-visibility events have focused attention on classified networks with a renewed emphasis on information protection within the information sharing paradigm. Organizations must strive to ensure responsible sharing and safeguarding of classified information by employing advanced capabilities that enable a common level of assurance in information handling and sharing while ensuring the interoperability required to satisfy mission requirements.

This Note describes a new combination of tactics by cyber criminals that disrupts telephone systems of targeted organizations. This information is provided to assist and inform the Department and federal, state, local, territorial, tribal, and private sector partners in mitigation efforts regarding criminal activity that could affect their operations.

The National Cybersecurity and Communications Integration Center (NCCIC) Resource and Capabilities Guide is intended to enhance cross-sector cyber security efforts and collaboration by better informing our cybersecurity and communications partners of the NCCIC’s tools, assets, and collaboration mechanisms offered. This guide also identifies the Center’s resources and capabilities as well as describes the processes for accessing NCCIC information portals and products, incident reporting systems, and relevant point of contact information for our community of partners.

As related to malware which may exhibit a potentially destructive capability, organizations should increase vigilance and evaluate their capabilities encompassing planning, preparation, detection, and response for such an event. Destructive malware presents a direct threat to an organization’s daily operations, directly impacting the availability of critical assets and data. In addition, the response required for such an event can be extremely resource intensive.

The following product is a coordinated effort between NCCIC, U.S. Secret Service and The Cyber Intelligence Network (CIN), provided to assist in prevention, detection and mitigation of a new ransomeware campaign. Ransomware is malware that restricts access to infected computers and requires victims to pay a ransom in order to regain full access. Cryptolocker is particularly interesting in that it functions by encrypting victims computer files with a combination of RSA-2048 and AES-256 encryption. Once encrypted, victims are provided a window of time in which they can pay the actors to receive the key needed to decrypt their files.

This Environmental Assessment (EA) has been prepared to analyze the potential environmental, cultural, transportation, and socioeconomic effects associated with the establishment and operation of a U.S. Army Cyber Command / 2nd Army (ARCYBER) Command and Control Facility at Fort George G. Meade, Maryland (hereinafter referred to as Fort Meade), or at Fort Gordon, Georgia. ARCYBER leads a corps of 21,000 soldiers and civilians who serve worldwide operating and defending all Army networks with supporting organizations such as the Army Network Enterprise Technology Command, 780th MI Brigade, and 1st Information Operations. ARCYBER plans, coordinates, integrates, synchronizes, directs, and conducts network operations and defense of all Army networks; when directed, ARCYBER conducts cyberspace operations in support of full spectrum operations to ensure U.S./Allied freedom of action in cyberspace, and to deny the same to our adversaries.
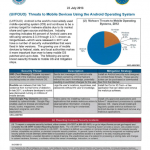
Android is the world’s most widely used mobile operating system (OS) and continues to be a primary target for malware attacks due to its market share and open source architecture. Industry reporting indicates 44 percent of Android users are still using versions 2.3.3 through 2.3.7-known as Gingerbread-which were released in 2011 and have a number of security vulnerabilities that were fixed in later versions. The growing use of mobile devices by federal, state, and local authorities makes it more important than ever to keep mobile OS patched and up-to-date.

Since June, advanced persistent threat (APT) actors have been targeting the aviation industry and attempting to extract confidential information by sending “spear-phishing” emails designed to trick recipients into opening malicious attachments or follow links to infected websites. According to an FBI Cyber Division bulletin from July 8, “individuals associated with the air travel industry” have received an increased number of spear-phishing emails often using spoofed senders “in an attempt to make the e-mail appear more legitimate.”

Since June 2013, the FBI has observed advanced persistent threat (APT) actors’ increased interest in the aviation industry. APT actors have sent spear-phishing e-mails targeting individuals associated with the air travel industry. Some of the spear-phishing e-mails originated from a spoofed sender in an attempt to make the e-mail appear more legitimate. E-mail recipients should be aware of suspicious and potentially malicious e-mail attachments or links.

DIB CS/IA is the DoD program to protect critical DoD unclassified program, technology, and operational information residing on, or transiting, DIB unclassified networks. DoD Components and industry participants collaborate to protect DoD information through the development, implementation, and execution of DoD and DIB processes and procedures.
State, local, tribal and territorial (SLTT) computer networks have been increasingly targeted by cyber adversaries. At the same time, the expansion of mobile devices integrated into SLTT networks provides new opportunities for cyber adversaries seeking to collect information or disrupt operations by compromising mobile technology and exploiting vulnerabilities in portable operating systems, application software, and hardware. Compromise of a mobile device can have an impact beyond the device itself; malware can propagate across interconnected networks.
Many networks run by public and private organizations have experienced intrusions in recent years, and this cyber exploitation has resulted in an unprecedented transfer of wealth due to lost intellectual property. The threats to our networks and systems exist across numerous components that include end-user-devices, servers, and infrastructure devices. To address threats to routers and other network infrastructure devices, the National Security Agency’s Information Assurance Directorate (IAD) is publishing this IAA to guide U.S. Government systems accreditors’ strategic plan for network hardening.
A Defense Security Service presentation from December 2012 outlining information and statistics on defense industrial base cyber incidents and intrusions.
Multiple groups, and individual hacker handles have claimed their intent to attack U.S. websites as part of OpUSA. As seen in many hacktivist operations (Ops), willing participants have posted free tools to assist other like minded individuals in their attack efforts. Often, more coordinated attacks will name a specific tool, target, day and time for the attack. That has not been the case for OpUSA thus far. Individual hacker groups seem to be conducting attacks independently, each claiming responsibility for individual defacements and data breaches that have supposedly recently taken place. Below you will find some of the tools being posted in conversations about OpUSA and links to US-CERT sites which provide background on the vulnerabilities exploited by these tools as well as mitigation advice for computer network defense actions.
Websites and emails referencing the Boston Marathon bombing should be viewed with caution, as malicious actors are using the incident to disseminate malware and conduct fraud. While other agencies investigate the frauds, the NJ ROIC provides this information for situational awareness.
A DHS presentation from March 11, 2013 regarding the implementation of Executive Order 13636 “Improving Critical Infrastructure Cybersecurity” authored by the Cyber-Dependent Infrastructure Identification Working Group (CDIIWG).
Terrorists or cyber criminals might try to discover vulnerabilities in computer systems by engaging in unauthorized testing of cybersecurity in order to exploit those vulnerabilities during an attack. These attempts might include port scanning, phishing, and password cracking. “Social engineering,” another technique, leverages unwitting insider access by eliciting information about operational and security procedures from employees, personnel, and their associates.
A document detailing investigative tools and materials utilized by the FBI when conducting cyber investigations. The document was distributed by the Oklahoma Bankers Association after being provided by a local branch of the FBI Cyber Division.