
A presentation from February 2014 providing an overview of the FBI National Data Exchange (N-DEx) system storing apprximately 223 million records on nearly 2 billion individual entities.

To prevent foreign entities from achieving their goals, a Counterintelligence Program (CIP) proactively searches for and uses information from multiple sources. An effective CIP draws information from security programs and other internal systems, as well as from the U.S. Intelligence Community (USIC). Once this information is assembled, an effective CIP develops a coherent picture and crafts a strategy to prevent the foreign entity from successfully achieving its goals and minimizes the damage already done. An effective CIP conducts active analysis of available information, requires annual CI education for all employees, and provides a system for immediate referral of behavior with CI implications.

Facility security measures, such as interior control points or exterior barriers, may require first responders to adjust normal protocols and procedures to operate rapidly during emergencies. The timeline below is an overview of attacks and plots against US-based facilities with varying levels of security. The diversity of tactics and targets used underscores the need for interagency exercises and training that incorporates multiple scenarios to account for building security measures likely to be encountered.

Since at least January 2012, criminals are using telephony-based denial-of-service (TDoS) combined with extortion scams to phone an employee’s office and demand the employee repay an alleged loan. If the victim does not comply, the criminals initiate TDoS attacks against the employer’s phone numbers. TDoS uses automated calling programs—similar to those used by telemarketers—to prevent victims from making or receiving calls.

In the first weeks of 2013, police officers were combing through a bloody scene in the Indian state of Jharkhand where a dozen security personnel had died in a shootout with local rebels. The Naxalite fighters, who promote a Maoist ideology through their ongoing guerrilla conflict with the Indian government, had killed the men, including five Central Reserve Police Force members, in a gun battle days before. When local villagers and police tried to remove the bodies, a bomb went off killing four more people. After the incident, a group of doctors in nearby Ranchi were performing an autopsy on one of the bodies when they encountered something metal lodged inside the body. A bomb squad was called in and an explosive device triggered by shifts in pressure that had been sewn into the police officer’s body was successfully defused.

Malicious cyber actors have used compromised social media accounts to spread disinformation about alleged emergencies and attacks, most prominently through Twitter. Because it is difficult to determine the authenticity of a tweet, we anticipate malicious cyber actors will continue to seek to exploit Twitter and other social media platforms used by news organizations and public safety agencies to propagate disinformation.

A joint bulletin issued in early August by the Department of Homeland Security and FBI warns state and local law enforcement agencies to look out for people in possession of “large amounts” of weapons and ammunition, describing the discovery of “unusual amounts” of weapons as a potential indicator of criminal or terrorist activity.

Possession of large amounts of weapons, ammunition, explosives, accelerants, or explosive precursor chemicals could indicate pre-operational terrorist attack planning or criminal activity. For example, in preparation for conducting the July 2011 attacks in Norway, Anders Behring Breivik stockpiled approximately 12,000 pounds of precursors, weapons, and armor and hid them underground in remote, wooded locations.

Over the past year, the NSI PMO has continued its implementation efforts and outreach to NSI stakeholders to help ensure that law enforcement and homeland security partners are afforded another tool to help identify and prevent terrorism and other related criminal activity. The ongoing collaboration among DOJ, DHS, the FBI, SLTT partners, and the National Network of Fusion Centers has strengthened, allowing the NSI to expand its nationwide information sharing capability. As of March 2013, 73 fusion centers have met the requirements outlined by the NSI PMO to be fully NSI-Operational—an increase of 5 centers from the same time last year—and all 78 fusion centers now maintain the capability to contribute and share suspicious activity reports through the Shared Space or eGuardian. This expansion of the NSI has allowed the Federated Search Tool to be accessed by more trained users—increasing the number of searches to more than 76,400—and more than 25,900 Information Sharing Environment (ISE)-SARs had been submitted and shared by the end of March 2013. Further, with the support of the National Network of Fusion Centers, 46 states and the District of Columbia are participating in statewide implementation of the NSI; implementation efforts are currently under way in Guam, Puerto Rico, and the U.S. Virgin Islands to ensure a strengthened nationwide capacity for sharing ISE-SAR information.

This Joint Intelligence Bulletin (JIB) provides information on the 21 September 2013 attack in Nairobi, Kenya likely conducted by al-Shabaab—an al-Qai‘da linked militant group based in Somalia. This JIB examines the ongoing incident and provides background on the threat from al-Shabaab. This JIB also highlights protective measures that can assist in mitigating threats in the United States using similar tactics and is provided to support the activities of FBI and DHS and to assist federal, state, local, tribal, and territorial government counterterrorism and law enforcement officials, as well as first responders and private sector security officials to deter, prevent, preempt, or respond to terrorist attacks in the United States or overseas targeting US interests.

Terrorists may engage in sabotage, tampering, or vandalism as part of an attack or to gain access to restricted areas, steal materials, or provoke and observe security responses. For example, the 1Oth edition of al-Qa’ida in the Arabian Peninsula’s Inspire magazine suggests torching parked vehicles and causing automobile accidents by using lubricating oil or nails driven through wooden boards as simple tactics to cause both casualties and economic damage.

Impersonation by assuming the identity, behavior, or appearance of first responders can allow terrorists access to restricted or secure locations, including the scene of emergencies when unchallenged. This access can allow terrorists the ability to conduct pre-operational surveillance or carry out a primary attack or a secondary attack against first responders. The method of impersonation may not be limited to the use of uniforms, clothing, badges and identification; civilian vehicles may be accessorized to appear as legitimate emergency vehicles.

An updated policy manual for the FBI National Data Exchange (N-DEx) released August 28, 2013. The manual was updated to include substantial additions to the regulations governing use of information within the system and the maintenance of records for later auditing of law enforcement agencies’ access to the system.

The Syrian Electronic Army (SEA), a pro-regime hacker group that emerged during Syrian anti-government protests in 2011, has been compromising high-profile media outlets in an effort to spread pro-regime propaganda. The SEA’s primary capabilities include spearphishing, Web defacements, and hijacking social media accounts to spread propaganda. Over the past several months, the SEA has been highly effective in compromising multiple high-profile media outlets.
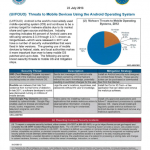
Android is the world’s most widely used mobile operating system (OS) and continues to be a primary target for malware attacks due to its market share and open source architecture. Industry reporting indicates 44 percent of Android users are still using versions 2.3.3 through 2.3.7-known as Gingerbread-which were released in 2011 and have a number of security vulnerabilities that were fixed in later versions. The growing use of mobile devices by federal, state, and local authorities makes it more important than ever to keep mobile OS patched and up-to-date.

Since June, advanced persistent threat (APT) actors have been targeting the aviation industry and attempting to extract confidential information by sending “spear-phishing” emails designed to trick recipients into opening malicious attachments or follow links to infected websites. According to an FBI Cyber Division bulletin from July 8, “individuals associated with the air travel industry” have received an increased number of spear-phishing emails often using spoofed senders “in an attempt to make the e-mail appear more legitimate.”

Since June 2013, the FBI has observed advanced persistent threat (APT) actors’ increased interest in the aviation industry. APT actors have sent spear-phishing e-mails targeting individuals associated with the air travel industry. Some of the spear-phishing e-mails originated from a spoofed sender in an attempt to make the e-mail appear more legitimate. E-mail recipients should be aware of suspicious and potentially malicious e-mail attachments or links.

In 2011, the U.S. Department of Homeland Security’s (DHS) Office of Intelligence and Analysis (I&A), in coordination with federal and SLTT partners, began conducting an annual assessment of fusion centers to evaluate their progress in achieving the COCs and ECs and to collect additional data to better understand the characteristics of individual fusion centers and the National Network as a whole. DHS/I&A initiated the 2012 Fusion Center Assessment (2012 Assessment) in August 2012 as the second iteration of the annual assessment process and the first assessment to provide data on year-over-year progress in implementing the COCs and ECs. The 2012 Assessment was also the first assessment to collect National Network performance data based on an initial set of five performance measures adopted in 2011. This 2012 National Network of Fusion Centers Final Report (2012 Final Report) summarizes and characterizes the overall capabilities and performance of the National Network based on the results of the 2012 Assessment. This report does not include fusion center-specific capability or performance data. Instead, it uses aggregated data from the 2012 Assessment to describe the capability and performance achievements of the National Network.
A collection of Network Security Agreements (NSAs) entered into with foreign communications infrastructure providers ensuring U.S. government agencies the ability to access communications data when legally requested. The agreements range in date from 1999 to 2011 and involve a rotating group of government agencies including the Federal Bureau of Investigation (FBI), Department of Homeland Security (DHS), Department of Justice (DoJ), Department of Defense (DoD) and sometimes the Department of the Treasury. According to the Washington Post, the agreements require companies to maintain what amounts to an “internal corporate cell of American citizens with government clearances” ensuring that “when U.S. government agencies seek access to the massive amounts of data flowing through their networks, the companies have systems in place to provide it securely.”