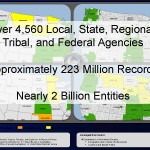
The Department of Defense has issued an instruction clarifying the rules for the involvement of military forces in civilian law enforcement. The instruction establishes “DoD policy, assigns responsibilities, and provides procedures for DoD support to Federal, State, tribal, and local civilian law enforcement agencies, including responses to civil disturbances within the United States.” The new instruction titled “Defense Support of Civilian Law Enforcement Agencies” was released at the end of February, replacing several older directives on military assistance to civilian law enforcement and civil disturbances. The instruction requires that senior DoD officials develop “procedures and issue appropriate direction as necessary for defense support of civilian law enforcement agencies in coordination with the General Counsel of the Department of Defense, and in consultation with the Attorney General of the United States”, including “tasking the DoD Components to plan for and to commit DoD resources in response to requests from civil authorities for [civil disturbance operations].” Military officials are to coordinate with “civilian law enforcement agencies on policies to further DoD cooperation with civilian law enforcement agencies” and the heads of the combatant commands are instructed to issue procedures for “establishing local contact points in subordinate commands for purposes of coordination with Federal, State, tribal, and local civilian law enforcement officials.”
Read more →