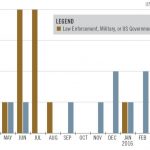
A bulletin from the El Paso Intelligence Center (EPIC) released to law enforcement in February 2017 describes how Mexican transnational criminal organizations (TCOs) are continuing to exploit legalized markets for the sale and distribution of marijuana. In January 2016, EPIC produced a bulletin detailing how “data provided by the Drug Enforcement Administration (DEA) and open source reporting” indicated that Mexican TCOs had not been adversely affected by marijuana legalization in numerous markets, noting instead “that the effort of legalization had conversely brought new opportunities for illicit profits from marijuana sales.”