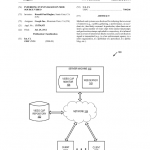
The law enforcement community often refers to their challenge in this context as “going dark.” In essence, “going dark” refers to advancements in technology that leave law enforcement and the national security community unable to obtain certain forms of evidence. In recent years, it has become synonymous with the growing use of strong default encryption available to consumers that makes it increasingly difficult for law enforcement agencies to access both real-time communications and stored information. The FBI has been a leading critic of this trend, arguing that law enforcement may no longer be able “to access the evidence we need to prosecute crime and prevent terrorism, even with lawful authority.” As a result, the law enforcement community has historically advocated for legislation to “ensure that we can continue to obtain electronic information and evidence pursuant to the legal authority that Congress has provided to keep America safe.”