
A series of videos derived from presentations posted on Prezi.com by FBI Criminal Justice Information Services Communications Officer Gene Weaver concerning the FBI’s Next Generation Identification program.

This Joint Intelligence Bulletin (JIB) provides information on the 21 September 2013 attack in Nairobi, Kenya likely conducted by al-Shabaab—an al-Qai‘da linked militant group based in Somalia. This JIB examines the ongoing incident and provides background on the threat from al-Shabaab. This JIB also highlights protective measures that can assist in mitigating threats in the United States using similar tactics and is provided to support the activities of FBI and DHS and to assist federal, state, local, tribal, and territorial government counterterrorism and law enforcement officials, as well as first responders and private sector security officials to deter, prevent, preempt, or respond to terrorist attacks in the United States or overseas targeting US interests.

Terrorists may engage in sabotage, tampering, or vandalism as part of an attack or to gain access to restricted areas, steal materials, or provoke and observe security responses. For example, the 1Oth edition of al-Qa’ida in the Arabian Peninsula’s Inspire magazine suggests torching parked vehicles and causing automobile accidents by using lubricating oil or nails driven through wooden boards as simple tactics to cause both casualties and economic damage.

Impersonation by assuming the identity, behavior, or appearance of first responders can allow terrorists access to restricted or secure locations, including the scene of emergencies when unchallenged. This access can allow terrorists the ability to conduct pre-operational surveillance or carry out a primary attack or a secondary attack against first responders. The method of impersonation may not be limited to the use of uniforms, clothing, badges and identification; civilian vehicles may be accessorized to appear as legitimate emergency vehicles.

An updated policy manual for the FBI National Data Exchange (N-DEx) released August 28, 2013. The manual was updated to include substantial additions to the regulations governing use of information within the system and the maintenance of records for later auditing of law enforcement agencies’ access to the system.

The Syrian Electronic Army (SEA), a pro-regime hacker group that emerged during Syrian anti-government protests in 2011, has been compromising high-profile media outlets in an effort to spread pro-regime propaganda. The SEA’s primary capabilities include spearphishing, Web defacements, and hijacking social media accounts to spread propaganda. Over the past several months, the SEA has been highly effective in compromising multiple high-profile media outlets.
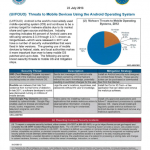
Android is the world’s most widely used mobile operating system (OS) and continues to be a primary target for malware attacks due to its market share and open source architecture. Industry reporting indicates 44 percent of Android users are still using versions 2.3.3 through 2.3.7-known as Gingerbread-which were released in 2011 and have a number of security vulnerabilities that were fixed in later versions. The growing use of mobile devices by federal, state, and local authorities makes it more important than ever to keep mobile OS patched and up-to-date.

Since June 2013, the FBI has observed advanced persistent threat (APT) actors’ increased interest in the aviation industry. APT actors have sent spear-phishing e-mails targeting individuals associated with the air travel industry. Some of the spear-phishing e-mails originated from a spoofed sender in an attempt to make the e-mail appear more legitimate. E-mail recipients should be aware of suspicious and potentially malicious e-mail attachments or links.
A collection of Network Security Agreements (NSAs) entered into with foreign communications infrastructure providers ensuring U.S. government agencies the ability to access communications data when legally requested. The agreements range in date from 1999 to 2011 and involve a rotating group of government agencies including the Federal Bureau of Investigation (FBI), Department of Homeland Security (DHS), Department of Justice (DoJ), Department of Defense (DoD) and sometimes the Department of the Treasury. According to the Washington Post, the agreements require companies to maintain what amounts to an “internal corporate cell of American citizens with government clearances” ensuring that “when U.S. government agencies seek access to the massive amounts of data flowing through their networks, the companies have systems in place to provide it securely.”

Fireworks are a common component used in Improvised Explosive Devices (IEDs). The US Government is asking consumer fireworks retailers to be aware of this phenomenon and familiarize themselves with some possible indicators of suspicious activity. This list is not inclusive, nor is it intended to limit the lawful conduct of innocent persons. The totality of behavioral indicators and other relevant circumstances should be considered.

Recent incidents in the Homeland demonstrate that consumer fireworks—widely used during the upcoming 4 July 2013 celebrations—can be misused by criminals and violent extremists to construct improvised explosive devices (IEDs). Consumer fireworks are defined as devices that produce audible and visible effects by combustion, containing between 50-130 milligrams of explosive material. They are banned in Delaware, Massachusetts, New Jersey, and New York.

Malicious actors may leverage the Internet to gain information against a potential target to support pre-operational planning efforts for kinetic or cyber attacks. Malicious actors can use Internet search engines for information such as maps, company photographs or blueprints, and gain additional details from social media sites and Web blogs. Some actors may use more sophisticated techniques—such as phishing, spear phishing, or actual penetration of an organization’s network or devices—which can be used to gather personal, sensitive, or proprietary data.

This Joint Intelligence Bulletin (JIB) provides information on the 16 May 2013 arrest of Idaho-based Uzbekistan national Fazliddin Kurbanov by the FBI Boise Joint Terrorism Task Force (JTTF). On 16 May, Kurbanov was charged under two indictments alleging terrorism, one each in the United States District Court, District of Idaho and United States District Court, District of Utah. FBI and DHS are providing this information to support their respective activities and to assist federal, state, local, tribal, and territorial government counterterrorism and law enforcement officials and the private sector in deterring, preventing, or disrupting terrorist attacks against the United States. All events described in this JIB are taken from the criminal indictment. The charges contained in the indictment are mere allegations. As in any criminal case, the defendant is presumed innocent until proven guilty in a court of law.
More than a dozen images originally published on the website Кавказская политика Kavkazskaya Politika (Politics of the Caucasus) after being displayed at a press conference held in Moscow by Ibragim Todashev’s father Abdul-Baki Todashev on May 30, 2013. Ibragim Todashev was shot seven times in his Orlando, Florida apartment on May 22, 2013 following eight hours of questioning by an FBI Special Agent from the Boston Field Office and at least one Massachusetts State Police trooper. Law enforcement sources have provided media outlets with several differing versions of the events leading up to Todashev’s death. First, sources described Todashev being shot after he reportedly attacked the FBI agent with a knife. In later accounts, Todashev was described as being unarmed. In the most recent version of events Todashev reportedly overturned a table, knocking the FBI agent to the ground, before lunging at the agent with a pole or broomstick.
State, local, tribal and territorial (SLTT) computer networks have been increasingly targeted by cyber adversaries. At the same time, the expansion of mobile devices integrated into SLTT networks provides new opportunities for cyber adversaries seeking to collect information or disrupt operations by compromising mobile technology and exploiting vulnerabilities in portable operating systems, application software, and hardware. Compromise of a mobile device can have an impact beyond the device itself; malware can propagate across interconnected networks.
Terrorists and violent extremists have used—or considered using—diversionary tactics in terrorist attacks overseas. Diversionary tactics are often used to draw security forces and first responders away from the intended primary target of the attack and may be used as part of a complex or multi-pronged attack. Diverting first responders to a location other than the primary target of an attack delays the response and the provision of medical care to victims, and depletes first responder resources.
Terrorists and violent extremists could use unsuspecting civilians to transport improvised explosive devices (IEDs) artfully concealed in seemingly harmless items for use in attacks in the Homeland. Overseas attacks demonstrate that violent extremists have successfully used unsuspecting individuals to carry items containing IEDs to specific targets where the devices are then detonated remotely. This tactic enables terrorists and violent extremists to place IEDs in secure areas, among large gatherings of people, or at high profile events and detonate them from a standoff distance.
Multiple groups, and individual hacker handles have claimed their intent to attack U.S. websites as part of OpUSA. As seen in many hacktivist operations (Ops), willing participants have posted free tools to assist other like minded individuals in their attack efforts. Often, more coordinated attacks will name a specific tool, target, day and time for the attack. That has not been the case for OpUSA thus far. Individual hacker groups seem to be conducting attacks independently, each claiming responsibility for individual defacements and data breaches that have supposedly recently taken place. Below you will find some of the tools being posted in conversations about OpUSA and links to US-CERT sites which provide background on the vulnerabilities exploited by these tools as well as mitigation advice for computer network defense actions.
Various cyber actors have engaged in malicious activity against Government and Private Sector entities. The apparent objective of this activity has been the theft of intellectual property, trade secrets, and other sensitive business information. To this end, the malicious actors have employed a variety of techniques in order to infiltrate targeted organizations, establish a foothold, move laterally through the targets’ networks, and exfiltrate confidential or proprietary data. The United States Department of Homeland Security (DHS), in collaboration with the Federal Bureau of Investigation and other partners, has created this Joint Indicator Bulletin, containing cyber indicators related to this activity. Organizations are advised to examine current and historical security logs for evidence of malicious activity related to the indicators in this bulletin and deploy additional protections as appropriate.
This Joint Intelligence Bulletin provides law enforcement and private sector safety officials with protective measures in light of the recent explosions that took place at the 2013 Boston Marathon in Boston, Massachusetts. The information is provided to support the activities of DHS and FBI and to assist federal, state, local, tribal, and territorial government counterterrorism and first responder officials and the private sector to deter, prevent, preempt, or respond to terrorist attacks in the United States.
This Joint Intelligence Bulletin provides information on the devices used in the 15 April 2013 Boston Marathon explosions. The information is intended to provide aid in identifying devices and to support the activities of DHS and FBI and to assist federal, state, local, tribal, and territorial government counterterrorism and first responder officials and the private sector to deter, prevent, preempt, or respond to terrorist attacks in the United States.
This is an update of an RCR published on 1 July 2010. Rudimentary improvised explosive devices (IEDs) using pressure cookers to contain the initiator, switch, and explosive charge frequently have been used in Afghanistan, India, Nepal, and Pakistan. Pressure cookers are common in these countries, and their presence probably would not seem out of place or suspicious to passersby or authorities. Presence in an unusual location—or if noticed in a contanier such as a backpack—should be treated as suspicious.
The FBI assesses with high confidence recreationally used exploding targets (ETs), commonly referred to as tannerite, or reactive targets, can be used as an explosive for illicit purposes by criminals and extremists and explosive precursor chemicals (EPCs) present in ETs can be combined with other materials to manufacture explosives for use in improvised explosive devices (IEDs).