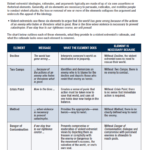
Russia’s invasion of Ukraine has spurred Western governments, social media companies, and individuals to limit or disengage from Russian state media outlets, likely degrading many outlets’ ability to directly message to Western audiences through 2022. This Western response impedes the ability of critical elements of Russia’s influence ecosystem to recruit and retain culturally adept media talent, shape in-country reporting, maintain a perception of media independence, and generate revenue. These setbacks affect multiple facets of RT’s and Sputnik’s operations, hampering the prospects for a speedy reconstitution of their Western-facing efforts. These actions, and others being considered by Western countries, go well beyond previous efforts to counter Moscow’s use of its state media outlets to spread mis-, dis-, and malinformation (MDM), such as deplatforming, foreign agent registration, and social media labeling of content.
Read more →