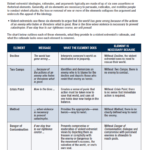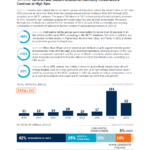
Terrorist and militant attacks on electric power infrastructure outside the United States in 2021 and 2022 occurred at more than three times the average annual number of attacks from 2015 through 2020, according to an NCTC database. The peak of 101 attacks in 2021 at least partly reflected incidents attributed to ISIS’s “economic war” campaign, judging from press reporting and terrorist social media. We expect the high rate of attacks to continue for the remainder of 2023 because of the accessibility and ongoing vulnerability of electricity infrastructure and the number of well-publicized attacks in 2021-22.