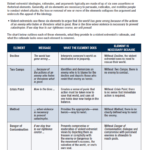
The following symbols are used by Anti-Government or Anti-Authority Violent Extremists, specifically Militia Violent Extremists (MVE). MVE symbols are often found on propaganda, online platforms, memes, merchandise, group logos, flags, tattoos, uniforms, etc. Widespread use of symbols and quotes from American history, especially the Revolutionary war, exists within MVE networks. Historic and contemporary military themes are common for MVE symbols. The use or sharing of these symbols alone should not independently be considered evidence of MVE presence or affiliation or serve as an indicator of illegal activity, as many individuals use these symbols for their original, historic meaning, or other non-violent purposes.